How To Secure Web Applications With AWS WAF
Introduction:
The world now runs on applications, from internet banking and remote work applications to entertainment delivery and e-commerce. It’s no surprise that attackers target programs as a key target, exploiting design flaws as well as gaps in APIs, open-source code, third-party widgets, and access control.
Modern cybersecurity attacks are undetectable and uncounterable by network layer firewalls and traditional security solutions. AWS provides the Web Application Firewall (WAF) and the AWS Shield to tackle such attacks and safeguard your application without having to manage the underlying infrastructure and application code of security solutions.
AWS WAF has the greatest market share in the worldwide cloud service industry. It is mostly used to protect websites against web application assaults. AWS Shield protects your CloudFront distributions, Amazon Route 53 hosted zones, and Elastic Load Balancers from DDoS attacks. Among other things, AWS WAF provides straightforward AWS integration, cost, and flexibility.
This article focuses on the following pointers:
- What is WAF?
- How WAF Works?
- Role of WAF
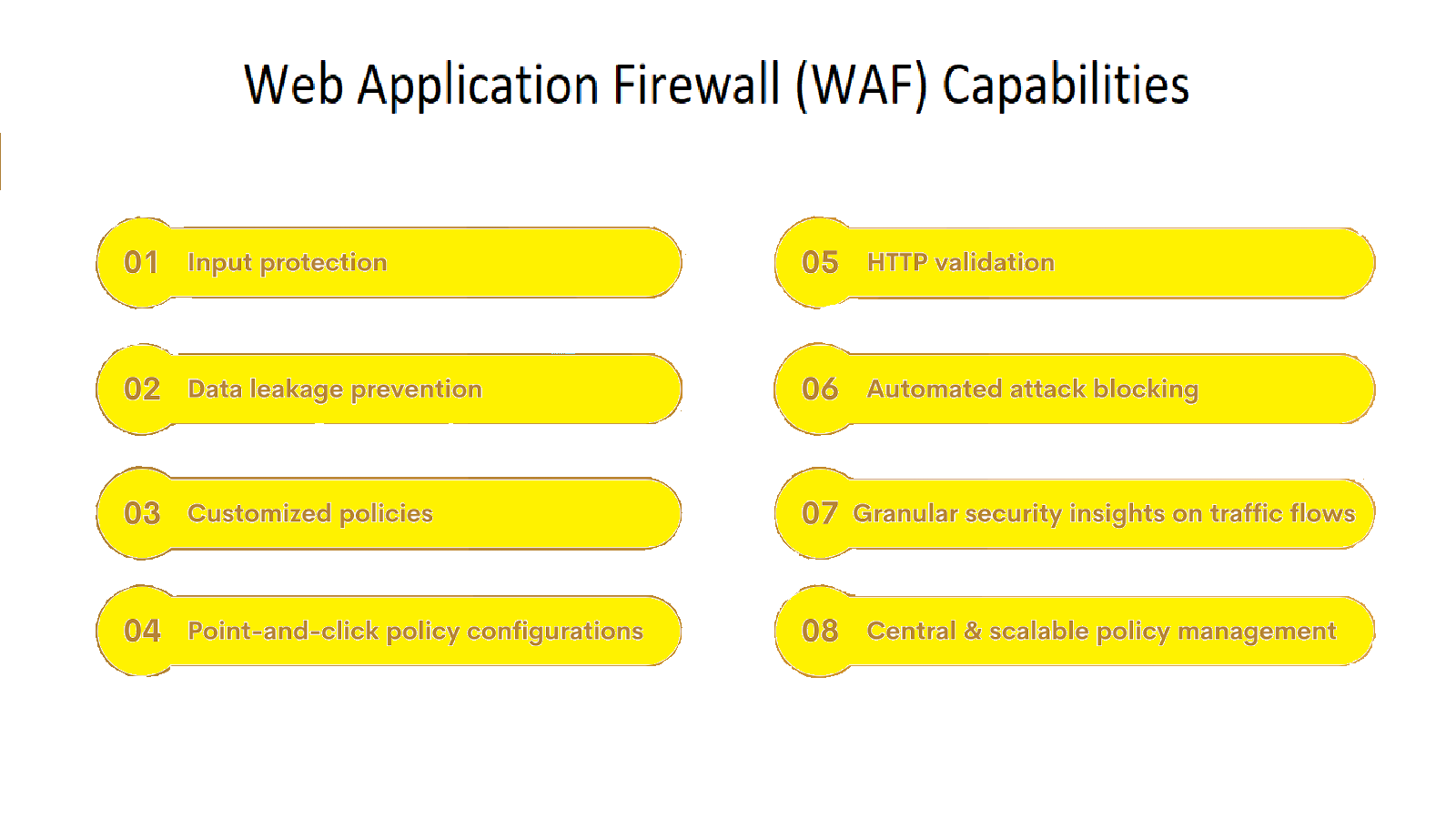
- Web Application Firewall (WAF) Capabilities
- How WAF handles bad requests
- Logging and Monitoring of WAF
- AWS WAF and AWS Shield Architecture
- Attacks that WAF prevents
- Hands-on
- Conclusion
What is WAF?
By filtering and monitoring HTTP traffic between a web application and the Internet, a WAF, or Online Application Firewall, aids in the protection of web applications. Cross-site forgery, cross-site scripting (XSS), file inclusion, and SQL injection are common attacks that it protects web applications against. A WAF (in the OSI model) is a protocol layer 7 protection that is not meant to fight against all forms of assaults.
How WAF Works?
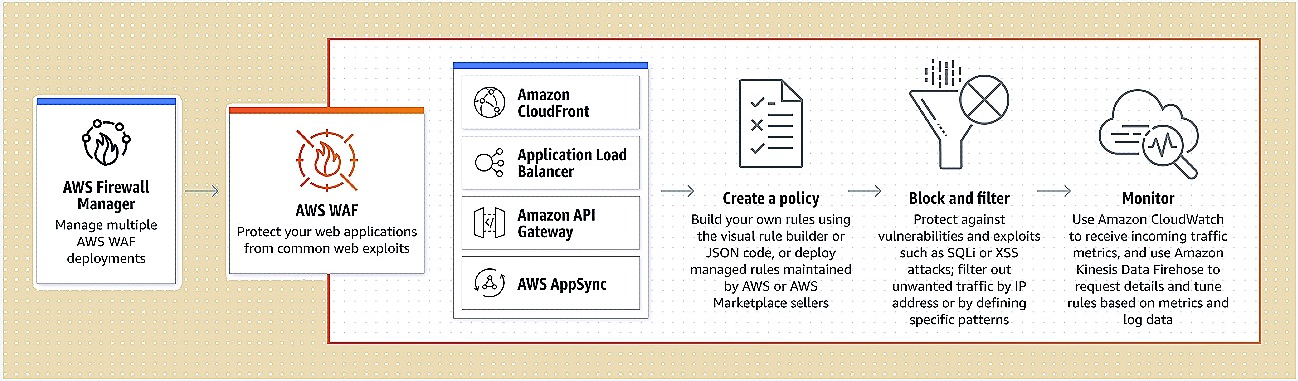
AWS WAF allows you to regulate how traffic enters your applications by allowing you to establish security rules that block typical attack patterns like SQL injection and cross-site scripting, as well as rules that filter out specific traffic patterns. Managed Rules for AWS WAF, a pre-configured set of rules managed by AWS or AWS Marketplace Sellers, will help you get started quickly. The OWASP Top 10 security threats are addressed by the Managed Rules for WAF. As new concerns arise, these guidelines are revised on a regular basis. AWS WAF comes with a comprehensive API for automating the generation, implementation, and management of security rules.
Role of AWS AWF
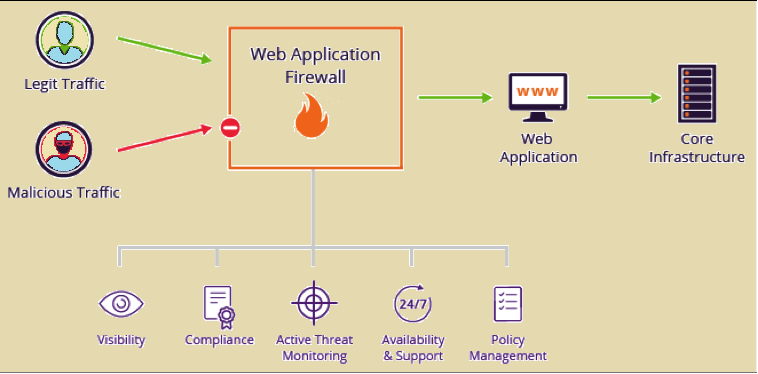
Web Application Firewall (WAF) Capabilities
WAF security can prevent many attacks, including:
- Cross-site Scripting (XSS) – Attackers inject client-side scripts into websites that are viewed by other users
- SQL injection – Inserting or injecting malicious code into a web entry field, allowing attackers to gain access to the program and its underlying systems.
- Cookie poisoning – It is the process of altering a cookie in order to get illegal information about a user for reasons such as identity theft.
- Unvalidated input – To get beyond the site’s security systems, attackers tamper with HTTP requests (including the URL, headers, and form fields).
- Layer 7 DoS – An HTTP flood attack that uses valid requests to retrieve data from normal URLs.
- Web scraping – Web scraping is a type of data scraping that is used to retrieve information from websites.
How does the WAF handle bad requests?
AWS WAF offers a number of components, including WEB ACLs, which you may construct and associate with your AWS services like CloudFront. These WEB ACLs are set up with rules that determine whether a request should be approved or rejected.
Logging and Monitoring of WAF
At any moment, you can activate or stop logging in for a web ACL. To log AWS WAF events, you can use CloudWatch or Amazon Kinesis. You may also create custom reports and take actions based on your own requirements.
AWS WAF and AWS Shield Architecture
DDoS is a malicious attempt to disrupt the normal traffic of a targeted server, service, or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic. AWS Shield provides always-on detection and automatic inline mitigations that minimize application downtime and latency, so you don’t need to engage AWS Support to benefit from DDoS protection. Custom WEB ACLs in AWS WAF can help you block or refuse requests that aren’t permitted, safeguarding your application’s integrity.
Attacks that WAF prevents
Terminologies to be familiar with while using WAF:
Web ACL
A web access control list (web ACL) allows you to fine-tune how your protected resource reacts to web requests. Amazon CloudFront, Amazon API Gateway, Application Load Balancer, and AWS AppSync resources may all be protected.
You may also test for any of these criteria in combination. You can block or count web requests that not only match the parameters but also surpass a certain number of requests in a 5-minute timeframe. Logical operators can be used to combine conditions.
Rule groups
A rule group is a set of rules that may be reused in a web ACL. See Managing and Using a Web Access Control List for further information on web ACLs (Web ACL).
There are two primary types of rule groups:
- AWS Managed Rules and AWS Marketplace vendors establish and maintain managed rule groups for you.
- You design and manage your own rule groups.
AWS WAF rules
Rules explain how to check web requests and what to execute when a web request fits the inspection criteria in each ruling group and web ACL. Depending on the rule and statement type, each rule requires one top-level statement, which may contain nested statements at any depth.
The inspection instructions are contained as rule statements in the JSON format, and the action is included as rule actions.
A web ACL’s rules are used to deny or allow web requests based on criteria such as these:
- Scripts with a high likelihood of becoming malicious. Scripts that can exploit vulnerabilities in online applications are embedded by attackers. Cross-site scripting is the term for this (XSS).
- Requests are sent from IP addresses or address ranges.
- The country or geographic location from which the requests come.
- The query string, for example, is the length of the given section of the request.
- SQL code has a high probability of being harmful. By injecting malicious SQL code in a web request, attackers attempt to harvest data from your database. SQL injection is the term for this.
- Values in the User-Agent header or text strings in the query string, for example, are strings that occur in the request. Regular expressions (regex) can also be used to specify these strings.
IP SET
In a rule statement, an IP set is a collection of IP addresses and IP address ranges that you want to utilize together. AWS resources are IP sets.
You must first establish an AWS resource, IPSet, with your address requirements before using an IP set in a web ACL or rule group. The set is then referenced when an IP set rule statement is added to a web ACL or rule group.
Regex pattern set
A regex pattern set is a set of regular expressions that you may employ in a rule statement together. AWS provides regex pattern sets.
You must first build an AWS resource, RegexPatternSet, containing your regex pattern specifications before using it in a web ACL or rule group. The set is then referenced when a regex pattern set rule statement is added to a web ACL or rule group. There must be at least one regex pattern in a regex pattern set.
When a regex pattern set comprises more than one regex pattern, the pattern matching is merged with an OR when it’s utilized in a rule. That is, if the request component meets any of the patterns in the set, the web request will match the pattern set rule statement.
Hands-on
In this hands-on, we will deploy a sample web application and implement WAF.
- We will use an AWS sample web application to demonstrate AWS WAF.
Go to the website: https://github.com/aws-samples/aws-bookstore-demo-app
Click Launch stack with your preferred region:
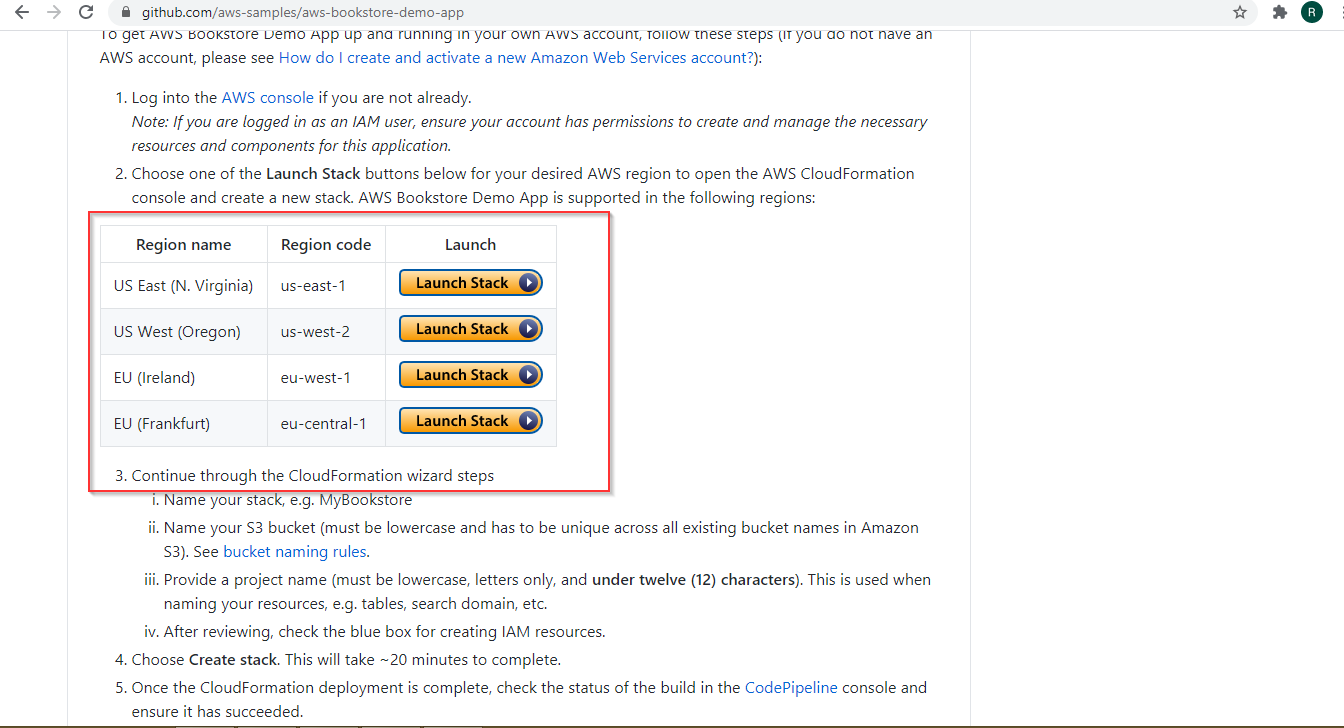
Click Launch stack.
You’ll be redirected to the CloudFormation page of AWS. You’ll need to provide some basic stack details as shown in the upcoming steps:

Specify stack details as shown below and click Next.

After filling out the stack details, click create a stack.

As you can see, the stack has been created. This will take 10-15 mins to complete. After successful creation, you’ll get a CloudFront URL in the outputs section to access the web application as shown below.

Now copy the URL and open it in your browser. The application will look like this:

Now that our web application is ready, let’s protect it using AWS WAF.
Go to AWS WAF and click Web ACLs as shown below:

Fill in the specifications as shown below and click next:

Select add rules as shown below:
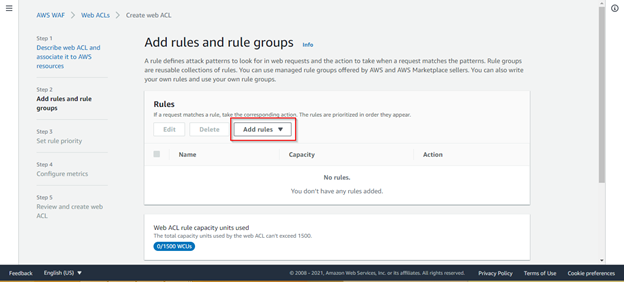
AWS provides some managed rules which are production ready. Here will be creating our own rules.
From the drop-down, select Add my own rules and rule groups:

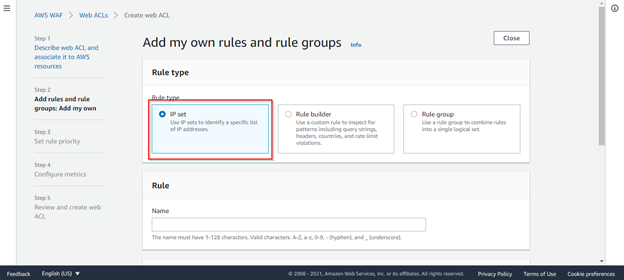
We will create two rules here to demonstrate WAF features:
- To block requests originating from specific sources we need to create an IP set.
- Block a particular URI path.
Steps to create an IP set:
Click create an IP set
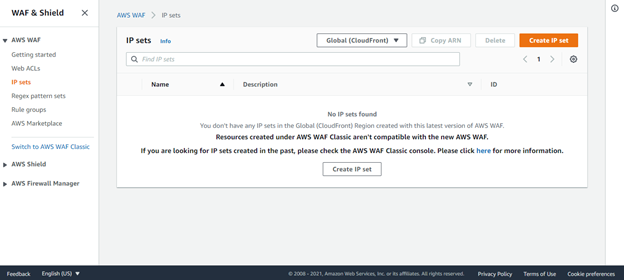
Provide the required details as shown below:
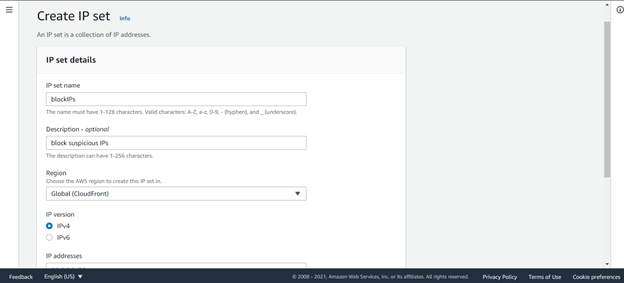
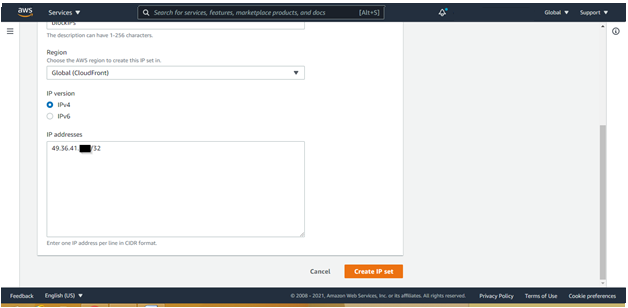
After successful creation. It will be shown in the main page as shown below:

Steps to create URI base rule:
Select rule builder and provide details as shown below

Select action as block and click add the rule as shown below.
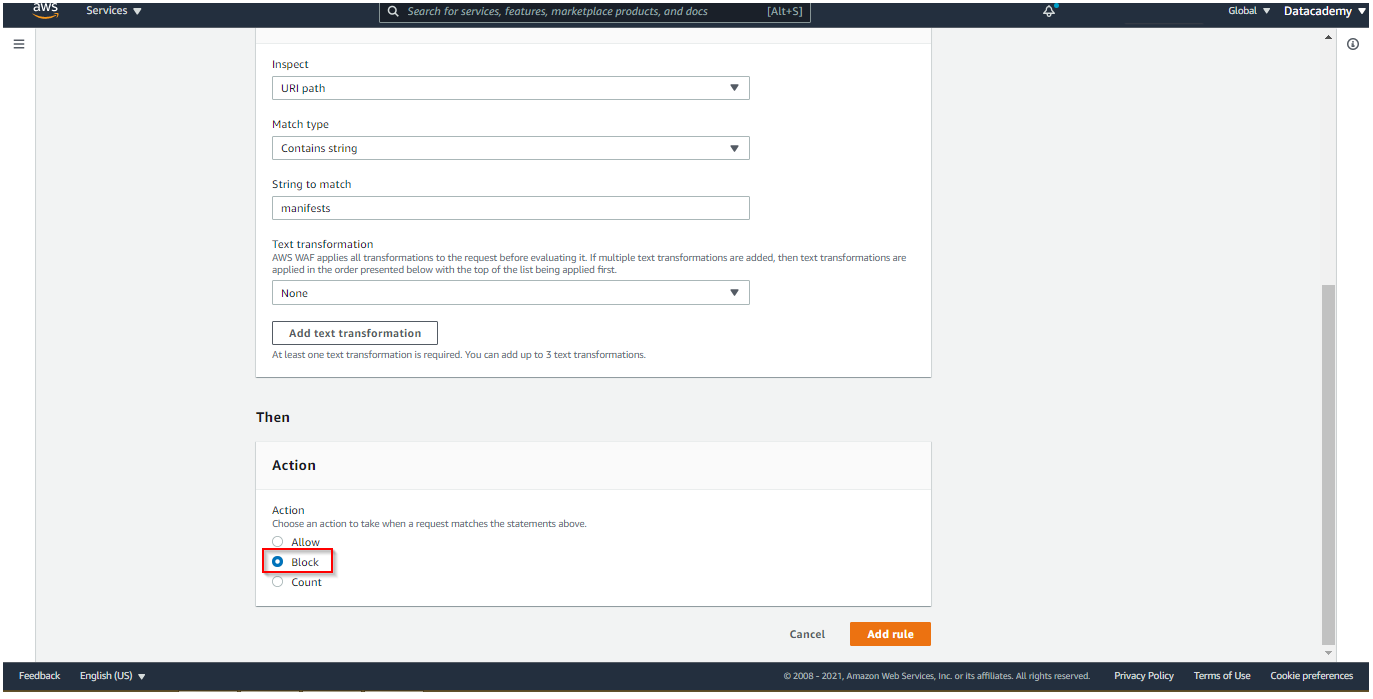
Go to the Web ACL dashboard and proceed with rules selection:
Select the rules created above as shown below:
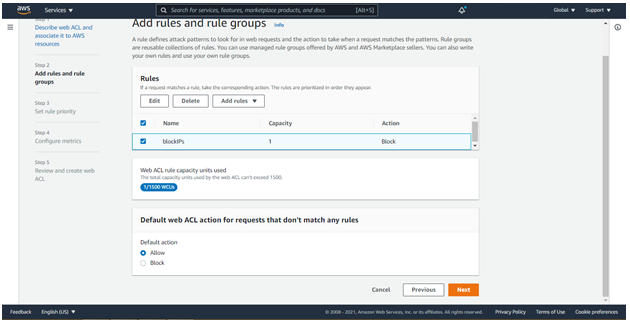
Select rule priority and click Next.
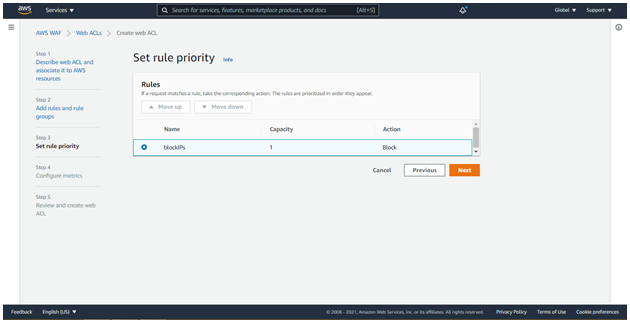
Click create web ACL.


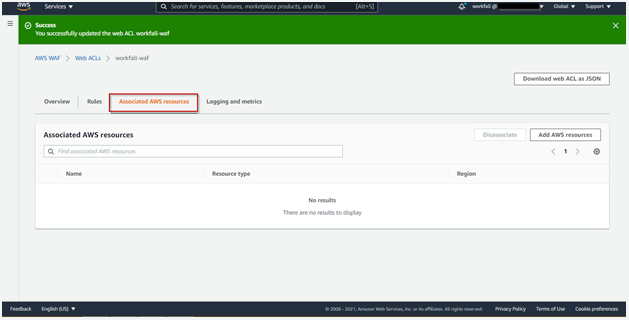
As you can see in the image below, WEB ACL has been successfully created.


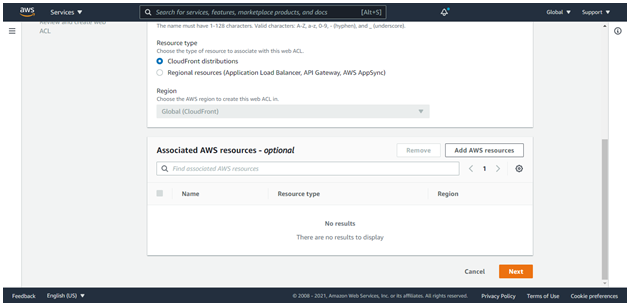
Now we need to specify AWS resources for our WEB ACLS.
Click on Associated AWS resources to add our CloudFront distribution:
Select the CloudFront distribution you want to apply as shown below:

Once this is done we are ready to test our rules.
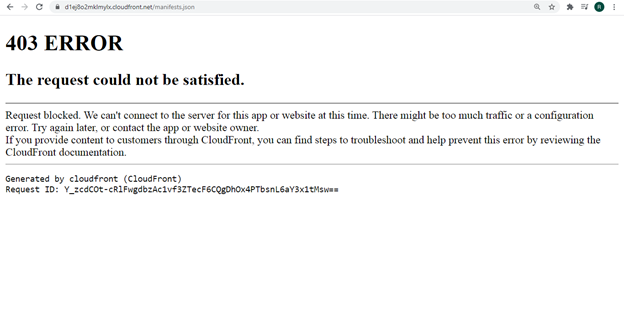
Open the CloudFront URL and try to access /manifests.json path, you should get access denied response as shown below.

You can see the sample requests and actions in the overview section as shown below:

So we have successfully seen AWS WAF in action and its use cases.
Conclusion
In this blog, we explored AWS WAF, how it works, how WAF handles bad requests, its logging, and monitoring, what attacks it prevents and saw how easy it is to use AWS WAF and protect our web application from threats and attacks. With our own custom rules and WEB ACLs, we can easily manipulate our traffic and allow or deny access to requests easily within a few clicks. We will discuss AWS WAF in our upcoming blogs. Stay tuned to keep getting all updates about our upcoming new blogs on AWS and relevant technologies.



