ITIL Interview Questions Answers for 2023
1. What is ITIL®?
ITIL® or Information Technology Infrastructure Library is a set of practices highlighting the best ways it can deliver the highest quality IT services. ITIL® also helps with:
- Managing business risks
- Strengthening customer relationships
- Establishing cost-effective practices
- Creating a stable IT environment and much more
2. What is ITSM?
ITSM or Information Technology Service Management is the act of taking the support of people, processes, and technology to deliver IT services and support internal customers.
3. Explain how Availability, Agreed Service Time, and Downtime are related.
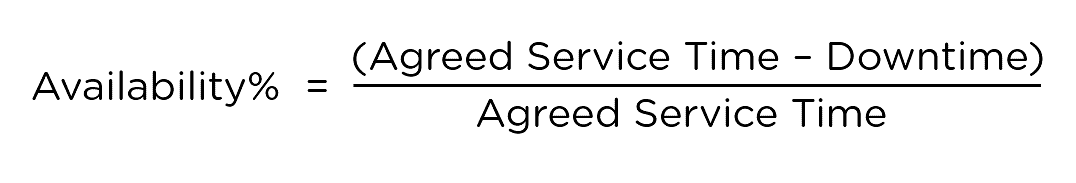
- Availability: It is the ability of an IT service or any of the other configuration items to perform its expected functions when required.
- Agreed Service Time: It is the expected time during which the service is to be operational.
- Downtime: It is the time during the agreed service time that your service isn’t operational.
4. What is an SLA?
SLA or Service-Level-Agreement is an agreement between the client and the service provider. It highlights the quality of service that the client expects from the provider, the metrics that make up the success being a success, and the penalties or remedies that the service provider would have to deal with if the service isn’t of the expected quality.
5. What are the types of SLAs?
- Corporate SLAs cover the issues relevant to the organization. These are the same across the organization.
- Customer SLAs refer to issues specific to the customers.
- Service SLAs deal with issues relevant to a specific service (in relation to the customer) that can be covered. Applies to all customers that contract the same service.
6. What are the Service Portfolio, Service Catalog, and Service Pipeline?
- The service portfolio is a repository of all the information related to the IT services in the organization.
- The service catalog consists of links to active services with the help of their service design package.
- The service pipeline includes references to services that are still not live yet. These plans could be proposed or under development.
7. What is a Service Request?
A service request is a request for IT service access, changing a standard, information, or advice. The service request usually covers things that have already been approved by company policy and don’t require any new additional permissions.
8. What are the types of Service Providers?
- Internal Service Providers: These represent the dedicated resources of a business unit and deal with organization management internally.
- External Service Providers: These providers provide services to external customers. They handle specific and special scenarios based on market standards.
- Shared Services: These are autonomous special units that act as internal service providers.
9. Explain the difference between an End-User and a Customer.
- End-user: A end-user is someone who directly receives or uses the product.
- Customer: A customer is someone who defines the requirements of service and may or may not be able to choose between products or suppliers.
10. What is a Standard Change?
Standard change refers to a change that’s been implemented in the form of a service request.
11. What is a Configuration Item?
A configuration item is a component that needs to be managed to deliver an IT service. It records information about these CIs into the configuration record, within the configuration management system. These items could be IT services, hardware, software, buildings, people, and other formal documentation.
Let’s take a look at some more ITIL® Interview questions.
12. Explain the phases of the ITIL® Lifecycle?

The different stages of the ITIL® life cycle are:
- Service strategy: It provides a plan/ strategy for the overall life cycle of the project. In this stage, it ensures the strategy to be in sync with the business’ objectives to ensure that the customers can derive value from the customers.
- Service Design: This stage involves the design of services and additional components that need to be introduced into the live environment.
- The next phase is the Service Transition. In this phase, IT services are built and deployed. It also ensures that changes to the service and service management process happen in a coordinated manner.
- Service Operations focus on making sure that the expectations of the end-user are met, making sure that costs and potential issues are managed.
- Continual Service Improvement involves quality management to learn from previous losses and successes. With this, the effectiveness and efficiency of IT processes and services can be improved.
13. What are the 4 Ps of ITIL®?
People: These represent the individuals who are associated with the processes and procedures.
Processes: The company’s ability to implement processes are focused on.
Products: These focus on the service itself, along with its underlying technology.
Partners: The partners who work with the IT organization to ensure that the service works properly.
14. Explain the Service Value System?
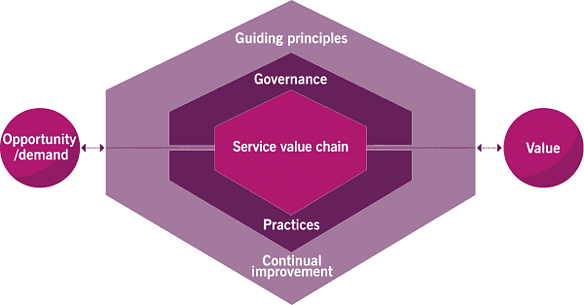
The service value system describes the different components and activities that synergize to create value. These include inputs, elements, outputs, and other components that are relevant to service management.
- Guiding principles: These are recommendations that can help an organization in any scenario, regardless of the aim, goal, strategy, type of work, management, or structure.
- Governance: It offers a structure that’ll help the organization establish and maintain control over its direction. It aims every investment the organization makes to create value and to ensure that they meet business objectives.
- Service Value Chain: It is a model used for creating, delivering, and continually improving services. It involves six activities, all of which can be combined in different ways to create multiple value streams.
- Practices: These are a collection of organizational resources that focus on performing some specific work or on fulfilling an objective.
- Continual Improvement: Focuses on the improvement by improving the service’s effectiveness and efficiency, reducing the cost of services, resources, and other IT management practices.
- Opportunity/Demand: Opportunity refers to the organization’s options to deliver value to its stakeholders and improve. Demand refers to the need/ desire for products among internal and external customers.
15. What are the Guiding Principles in the Service Value System?
We design the guiding principles to guide the organization’s decisions and actions to make sure they can make the most of ITIL®. These principles work regardless of the scenario, objective, goal, strategy, type of work, management, or structure. The seven guiding principles are:
- Focus on value
- Start where you are
- Progress iteratively with feedback
- Collaborate and promote visibility
- Think and work holistically
- Keep it simple and practical
- Optimize and automate
16. Explain the objective of ‘Design and Transition’ on the Service Value Chain.

The service value chain consists of 6 activities that enable the creation of value. The design and transition component will help organizations ensure the products and services are up to the quality, cost, and other requirement standards set by the stakeholders.
Intermediate ITIL® Interview Questions
17. Why do we need to ‘Engage’ as part of the Service Value Chain?

The engage component provides an understanding of the stakeholders’ needs, ensuring transparency, regular engagement, and a favorable relationship with the stakeholders.
18. Explain the role of Service Operation in ITIL®.
In this stage, we measure the value of IT Services. They also help:
- To deliver and support IT services at a satisfactory level for everyone involved in the process.
- To act as a point of contact, in the form of the service desk.
- To identify activities that need to be completed within the service catalog.
19. What are the measures of IT Service Management?
ITSM helps manage and control outcomes along with service operations, there are four measurement layers.
- Progress: This layer deals with the progress of the current service operations.
- Compliance: This layer focuses on existing industry processes and market standards.
- Effectiveness: This layer makes sure that it maintains the effectiveness of the service.
- Efficiency: This is the layer that focuses on maintaining the workflow and performing service maintenance.
Let’s continue having a look at some ITIL® interview questions
20. What is a Warranty?
A warranty is an assurance provided by the service provider to the customers/stakeholders that their products/services meet the agreed-upon requirements. It focuses on ‘how the service performs’ and to find whether services are ‘fit for use.’ It typically focuses on the service’s availability, security, capacity, and continual ensured working.
21. What is the Service Desk?
The service desk acts as a point of contact between the service provider and the users. It acts as a communication point where users can report operational issues, queries, and other requests. For the service desk to be successful, the service desk needs to have great customer service skills like empathy and emotional intelligence.
22. What are the responsibilities of a Service Desk?
- To ensure that it restores normal operations in the event of a disruption.
- To detail the steps to improve user awareness regarding IT issues and to encourage them to use IT services, components, and resources.
- To assist other IT Service Management processes and functions by escalating requests.
23. What is an IT asset?
An IT asset represents any component that’s financially valuable that eases the delivery of an IT product or service.
24. What is Problem and Problem Management?
A problem is a cause of conflict or incident which is still unknown. Problem Management is a process that manages the life-cycle of problems. Detecting and providing solutions or workarounds are considered a success to ensure the organization’s impact is limited and doesn’t recur.
The phases of problem management are:
- Problem identification
- Problem control
- Error control
25. What are the outcomes in ITIL®?
Outcomes are results obtained after performing an activity, following an activity, providing a service, and more. It is used to compare the intended and actual results. Outcomes are both qualitative and quantitative. We measure outcomes based on the perspectives of the people who are using the service.
26. What is a Utility?
A utility refers to a product/service’s functionality to meet a particular need in the market. A utility focuses on what a particular service does and finds if the service is ‘fit for its purpose.’
27. Explain how incidents, problems, and known errors are different from one another.
- Incidents: These are parts of the process that were not expected during the planning phase and not were supposed to be part of the standard operation.
- Problem: It is a cause of conflict or incidents which is still unknown.
- Known errors: A known error is a problem that’s already been diagnosed, and a workaround or a permanent solution has already been found.
28. What is a Workaround?
A workaround is a temporary solution that resolves issues temporarily. In this case, the issue’s reason has not been identified. The time frame for a workaround isn’t usually defined and could range from a few seconds to many years.
29. What are some workaround or recovery options?
Recovery options are divided into three categories:
- Fast recovery: This recovery takes place within 24 hours (hot standby).
- Intermediate recovery: The recovery process is completed within 3 days (warm standby).
- Gradual recovery: The recovery takes place in a matter of days/weeks, but always after 24 hours.
30. Explain the 7R’s of Change Management?
Change Management in ITIL® enables organizations to deploy changes without causing any downtime or any other disruption.
The 7 R’s are:
- Who RAISED the change?
- What is the REASON for the change?
- What RETURN will the change deliver?
- What RISKS are there if the change isn’t carried out?
- What are the RESOURCES required to perform the change?
- Who is RESPONSIBLE for this change?
- What is the RELATIONSHIP between this and other changes?
Moving forward in this article on ITIL® Interview Questions, we’ll cover topics like emergency changes, change enablement, PDCA cycle, PIR, and so on.
31. What is Emergency Changes?
Emergency changes are changes that need to be incorporated as soon as possible. The changes, in this case, aren’t tested, and it makes certain decisions balancing risks and rewards
32. What is Change Enablement?
It is the method that aims to maximize the number of IT changes that are successful by ensuring risks are assessed properly; it allows changes to proceed, and to manage the change schedule.
33. What’s the difference between a Change Request and a Service Request?
- A change request is a formal proposal to make alterations to a product/system made by a service user/ stakeholder.
- A service request is a request for IT service access to change a standard, information, or advice. These are things that are already approved by company policy.
34. What does a Known Error mean in ITIL®?
A known error refers to a problem that has been analyzed and has not been resolved.
35. Explain the plan-do-check-act (PDCA) cycle.
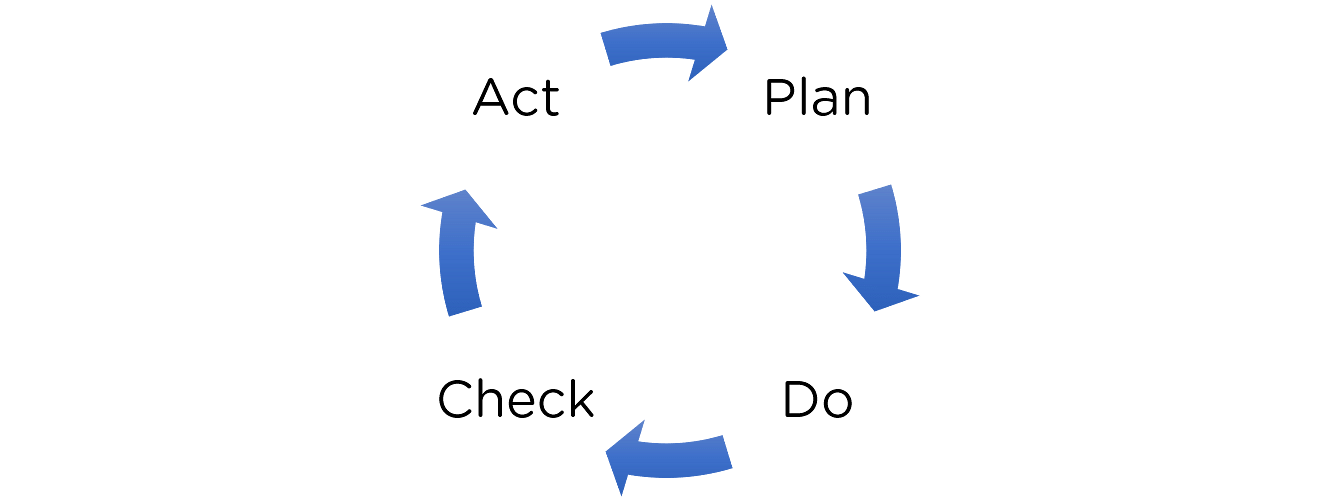
Businesses use the PDCA cycle for the control and continuous improvement of products and processes. The parts of the cycle are:
- Plan: In this stage, the improvements are planned. Here the measure of success is measured. After performing gap analysis, it makes a plan to reduce the gap through improvements
- Do: This stage involves the implementation of improvements. It is in this stage that we take steps to close the gaps determined in the previous phase
- Check: This stage involves monitoring, measuring, and reviewing. The results obtained here are compared to the factors that make up success, discussed in the planning stage
- Act: In this stage, the improvements identified are completely implemented
Intermediate ITIL® Interview Questions For Experienced
36. What is the Post Implementation Review?
The post-implementation review or PIL is an evaluation and analysis of the final working solution. After a change request is made, the review takes place and checks if the change and its implementation were successful. PIL helps answer questions like:
- Did the change solve the problem it aims to address?
- In the case of failure, did the back-out plan work?
- Did the change impact the customers?
- Were resources allocated effectively through the process?
- Was the change implemented based on a budget and in a timely manner?
37. What is the RACI model?
The RACI Model is a tool that helps identify different roles and responsibilities with ease during a project. It stands for:
- Responsible: The people who perform the work to complete the task. Depending on their tasks, responsibilities are assigned to them.
- Accountable: The person or people responsible for the thorough and correct completion of the task.
- Consulted: The person or people who provide information about the task and are consulted as it progresses. This usually involves back-and-forth communication.
- Informed: These people are kept informed regarding how the task is progressing. Communication, in this case, is usually one-way.
38. What is Incident Management, and what are its objectives?
Incident management is part of the IT Service Management that ensures normal service is restored as soon as possible. The objectives of incident management are:
- Reporting and resolving the incident with the IT service as soon as it happens.
- Focusing on the satisfaction of customers and users.
- Ensuring that approved and regulated methods are applied to all processes.
39. What is Service Request Management?
This practice focuses on the service’s agreed quality by managing service requests in an effective and user-friendly manner. These depend on processes and procedures to maximize the efficiency of the practice with the help of tracking and automation tools
40. What is the purpose of Supplier Management?
This form of management makes sure that the organization’s suppliers and their performance are properly supported to ensure continuous quality products and services. The objectives of supplier management are:
- To maintain the supplier contracts database
- Maintaining the supplier relationship
- Negotiating and establishing contracts with suppliers
41. What is the Continual Improvement Model?
This model defines a series of steps for implementing improvements. The model is known for using techniques like a SWOT analysis. It also uses balanced scorecard reviews, and maturity assessments. It provides a high-level guide to support improvement initiatives. With this, the chances of the ITSM initiative to be successful are improved. It places a stronger focus on customer value and making sure improvements match the organization’s vision.
42. Name some knowledge management systems related to ITIL®.
- CMIS (Capacity Management Information System): A Capacity Management Information System, or CMIS, collects information regarding IT infrastructure usage, capacity, and performance. The data is gathered in a consistent manner then stored in either a single or series of databases.
- AMIS (Availability Management Information System); The AMIS is a virtual repository of all Availability Management data and is usually stored in multiple physical locations.
- KEDB (Known Error Database): Known Errors are managed by the Problem Management process, with the details of each known error recorded in a Known Error Record, which is in turn stored in the Known Error Database (KEDB).
43. Why do we need Relationship Management?
Relationship management ensures that the organization’s suppliers and their performance are managed appropriately to support seamless, quality products, and services. Its major objective is to establish and nurture the links between the organization and its stakeholders
44. Why do we need Information Security Management Systems?
Information Security Management Systems help align business and IT security while also ensuring information is handled effectively across services and service management activities. These ensure that:
- Information is available and can be used when required. It also plays a role in ensuring that these systems can resist, recover, or prevent failures.
- Access to information is only for individuals who have the right to know it.
- The information is complete, accurate, and safe from unauthorized access.
- We can trust information exchange or business transactions.
45. What is the purpose of the deployment management practice?
The deployment management practice is used to move new or changed hardware, software, documentation, processes, or any other component to a live environment. They can also involve it in deploying components to other environments for the process of testing and staging.
46. Why do we need Relationship Management?
Relationship management ensures that the organization’s suppliers and their performance are managed appropriately to support seamless, quality products, and services. Its major objective is to establish and nurture the links between the organization and its stakeholders
47. Why do we need Information Security Management Systems?
Information Security Management Systems help align business and IT security while also ensuring information is handled effectively across services and service management activities. These ensure that:
- Information is available and can be used when required. It also plays a role in ensuring that these systems can resist, recover, or prevent failures.
- Access to information is only for individuals who have the right to know it.
- The information is complete, accurate, and safe from unauthorized access.
- We can trust information exchange or business transactions.
48. What is the purpose of the deployment management practice?
The deployment management practice is used to move new or changed hardware, software, documentation, processes, or any other component to a live environment. They can also involve it in deploying components to other environments for the process of testing and staging.
49. What is the difference between Utility and Warranty?
The utility is the ability of a service or product to fulfill a certain requirement. Perhaps utility responds to the question of ‘what the product accomplishes’ or if the service is ‘up to standard’. In contrast, a warranty is a guarantee that a service or product will satisfy agreed-upon specifications. Warranty addresses if a product is ‘fit for use’ or ‘how well the service operates.
50. What is the significant difference between ITIL® v2 and ITIL® v3?
When compared to ITIL® V2, which focuses on services generated by the firm, the process of creating them, and the persons who utilize them, ITIL® V3 focuses on the partners who are involved in the project. In addition, ITIL® V2 is a process-oriented strategy, while ITIL® V3 is a lifecycle-based essential part Of project management.
51. What is Incident Management, and what are its objectives?
Incident management is part of the IT Service Management that ensures normal service is restored as soon as possible. The objectives of incident management are:
- Reporting and resolving the incident with the IT service as soon as it happens.
- Focusing on the satisfaction of customers and users.
- Ensuring that approved and regulated methods are applied to all processes.
52. What is Service Request Management?
This practice focuses on the service’s agreed quality by managing service requests in an effective and user-friendly manner. These depend on processes and procedures to maximize the efficiency of the practice with the help of tracking and automation tools
53. What is the purpose of Supplier Management?
This form of management makes sure that the organization’s suppliers and their performance are properly supported to ensure continuous quality products and services. The objectives of supplier management are:
- To maintain the supplier contracts database
- Maintaining the supplier relationship
- Negotiating and establishing contracts with suppliers
54. What is the Continual Improvement Model?
This model defines a series of steps for implementing improvements. The Continual Improvement model is known for using techniques like a SWOT analysis. It also uses balanced scorecard reviews, and maturity assessments. It provides a high-level guide to support improvement initiatives. With this, the chances of the ITSM initiative to be successful are improved. It places a stronger focus on customer value and making sure improvements match the organization’s vision.
55. Name some knowledge management systems related to ITIL®.
- CMIS (Capacity Management Information System): A Capacity Management Information System, or CMIS, collects information regarding IT infrastructure usage, capacity, and performance. The data is gathered in a consistent manner then stored in either a single or series of databases.
- AMIS (Availability Management Information System); The AMIS is a virtual repository of all Availability Management data and is usually stored in multiple physical locations.
- KEDB (Known Error Database): Known Errors are managed by the Problem Management process, with the details of each known error recorded in a Known Error Record, which is in turn stored in the Known Error Database (KEDB).
56. ITIL v4 incident management process
Incident Management is described as a service management practice in ITIL V4, with core actions, inputs, outputs, and roles. Organisations should build a procedure for addressing incidents tailored to their specific needs based on this advice.
57. The service transition process focuses on?
Building and deploying IT services is the focus of the ITIL Service Transition Process.
58. What is the difference between ITIL and COBIT?
The Information Technology Infrastructure Library (ITIL) is a set of guidelines for managing information technology services. It gives you the ability to put the company’s policies into action.
COBIT (Control Objectives for Information and Related Technologies) is an information and technology integration framework. It allows us to create business operations norms.
59. What are the benefits of ITIL?
The following are some of the primary advantages of ITIL:
- Ensures that the business and IT departments are on the same page.
- Provides the greatest service management practices.
- Defines each task’s role in detail.
- Reduces expenses and improves resource use.
60. List the main steps in the Problem Management process.
- Identifying the issue
- The problem’s classification and priority
- Identifying the root reason
- Create a workaround for the situation
- Creating a known error record.
- Dealing with the problem
- Solve the issue
61. List the objectives of the IT Service Continuity Management.
The following are the goals of IT Service Continuity Management:
- Examine the risks involved.
- Experiment with backing out of situations.
- Make final preparations for the backout.
62. What is Configuration Management’s purpose in ITIL?
Configuration Management is the process of keeping track of all of a company’s hardware and software. Consider a large company with a lot of computers, software, and mobile devices. Someone must oversee this and keep track of the company’s IT assets.
63. What is the difference between a project and a process?
A project is a term that refers to the creation of something new or the implementation of a change. A process, on the other hand, tries to create value by completing a task repeatedly. A project has a set duration, but a process is ongoing and has no set end date.
64. Differentiate between proactive and reactive problem management.
The goal of reactive problem management is to solve problems as a result of one or more incidents. Proactive problem management is focused on finding and resolving problems and known faults before they cause new incidents.
65. What is the objective of Change Management in ITIL®?
Change management seeks to control the change process and, presumably, reduce the number of issues that arise as a result of it. Following that, the change manager will review and approve the modification. If the change is significant, it will be presented to a regular meeting of a change advisory board.
66. Explain Capacity Management’s main objective and mention its sub-processes.
Capacity management is the act of ensuring that IT capacity can provide consistent and acceptable service levels at a predictable and controllable cost.
Subprocesses are:
- Business Capacity Management
- Service Capacity Management
- Component Capacity Management
67. Define Operational Level Agreement (OLA).
The Operational Level Agreement (OLA) is a contract that focuses on the various IT groups inside a firm and how they construct their services to meet SLAs.
68. What is the difference between customers and end-users?
The service or product is received or used directly by the end-user or end customer. However, a customer may or may not be able to select from a variety of products and vendors.
69. What is the importance of an information security policy?
An information security policy helps to protect against cyber threats. Consumer trust is swiftly eroded by security incidents like data leaks and breaches. A robust information security policy can help prevent this kind of incident while still maintaining high levels of client confidence.
70. What is the objective of a Balanced Scorecard?
A balanced Scorecard lets businesses consolidate data into a single report and assists in the improvement of efficiencies.
71. What is a Change Advisory Board (CAB)?
The CAB (Change Advisory Board) is an authorised group of individuals charged with evaluating all high-impact Requests for Change from both a commercial and technical standpoint.
72. What is a Freeze period in ITIL®?
During the freeze period, no changes to the production system are permitted. It ensures that the service is not disrupted by the new adjustments. It frequently happens right before and right after a release goes live.
73. What are the ITIL models adopted by an organisation?
- Microsoft
The Microsoft Operations Framework is a set of instructions designed to assist IT professionals in establishing and implementing dependable, cost-effective services.
- IBM
The IT Process Model defines enterprise-wide business services and procedures. It aids in the renewal and integration of existing systems.
74. Give examples of proactive problem management.
- Keep tabs on incidents and problems.
- Researching customers.
75. What is the Configuration baseline?
In ITIL®, a configuration baseline is one that has been officially settled on and overseen through the change of the board cycle and is solely utilised for that setup.
76. What is ISO/IEC 27002?
The International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) developed ISO/IEC 27002 as an information security standard. This code of practice outlines information security principles and management procedures for organisations.
77. What is RACI-VS?
RACI-VS stands for: Verifies Sign off – The person who signs off on the project after ensuring that the acceptance criteria have been met.
78. What do you understand about Service Transition?
The techniques and processes of ITIL Service Transition assist enterprises in ensuring continuous service improvement and operations. The term “service transition” refers to the process of ensuring that a newly developed and improved service fulfils both customer and company expectations. The transition lifecycle stage is the step of a company’s movement from one state to another.
79. Why is Service Transition used?
- Plan and manage service changes in a timely and efficient manner.
- Manage the risks associated with new services that have been introduced, updated, or withdrawn.
- Ascertain if the service changes provide the anticipated value to the company.
- Deploy the service releases to environments that are capable of supporting them.
- Establish reasonable expectations for the performance and use of new or modified services.
- It guarantees that newly launched or changed services are simple to maintain and cost-effective over time.
80. Explain CSI.
CSI ensures that following a service outage, IT services may recover and continue. Assists in the completion of simplified business analysis in order to prioritise company recovery.
81. List down the 7 steps involved in CSI.
The following are the seven steps involved:
- Determine an improvement approach.
- Define the metrics that will be used.
- Collect the information
- Analyse and process the information and data
- Present and make use of the data
- Improve the situation.
82. What is Financial Management?
Financial management encompasses all functions and features of a company’s or an individual’s financial components. This encompasses, but is not limited to, financial and economic structure design, management, control, and evaluation for a customer.
In order to maximise profit and minimise expenditures, the financial management of a company necessitates developing a strategy to ensure that the firm’s finances continue to expand in a good direction.
83. Why is ITIL required?
ITIL is required for the following reasons:
- Enhance the success of project completion.
- Manage continual business, and IT changes.
- Give customers the most bang for their buck.
- Increase resources and capacities.
- Provide useful and dependable services.
- For each task, clearly specify roles.
- Provide services that add value to customers.
- Integration of business and service strategy.
- Enhance your customer relationship.
- Best practices for service management.
84. What are the advantages of ITIL?
Advantages of ITIL are:
- Provides dependable and beneficial services
- Improves service delivery success by providing a better customer experience
- Based on a single set of terms and a single language
- Consistently high quality
- The ability to integrate data
- Process automation skills that are strong
- Flexibility in deployment
85. Define Service Level Agreement
Service Level Agreements (SLAs) describe the connection between an IT Service Provider and the company that is seeking the provider’s services.
86. Mention layers of service management measurements.
- You’re in charge of overseeing the current service operations’ progress.
- Compliance refers to adhering to market norms and following industry trends.
- Effectiveness contributes to the services’ continued effectiveness.
- Workflow efficiency and service upkeep are aided by this feature.
87. Mention 7 steps involved in continual service improvement
The following are the seven steps involved in continual service improvement:
- To improve, find a focus.
- Understand what you’ll be measuring.
- Gather the information required.
- Organising data
- Investigate data and information.
- Information should be used wisely.
- Make the required changes.
88. List some popular web-based service desk tools.
Some popular web-based service desk tools are:
- HappyFox.
- Help Scout.
- SolarWinds Service Desk.
- JIRA Service Management.
- Salesforce Service Cloud.
- SysAid.
- Vivantio.
- Zoho Desk.
89. Explain Return on Investment
The ability to use assets to generate more value is measured by return on investment. Return on investment (percentage) = Net profit / Investment x 100 is a formula that may be used to determine it.
90. Define the concept of IT policy
The association’s Information Technology (IT) Policy lays out rules, guidelines, and rules for the appropriate use and support of the mechanical resources to guarantee the moral and satisfactory utilisation of information, items, and offices, as well as the wellbeing, security, and safety of the individuals who use them.
91. Define Service Reporting
The Service Reporting process documents both operational and strategic accomplishments. Its goal is to deliver information to both IT and the business so that they may make educated decisions. The format and style of reports should be agreed upon by IT and the business to suit their respective audiences.
92. Explain the term Service Assets and Configuration Management
Service asset management is concerned with the assets used to provide IT services. Configuration management is the process of keeping track of the configurations and interactions between the various components of your various IT services.
SACM involves having the option to recognise and administer all resources across your framework, as well as dealing with their integrity through compelling recording, detailing, and reviewing.
93. Differentiate between service and product
Products are things or systems made available for customer use, whereas services are transactions in which no actual goods are exchanged. The major distinction between a product and a service is that a product is tangible, whereas a service is intangible.
94. What is the reason for employing a balanced bundle of service metrics?
It provides an outcome-based view of services.
95. Why should incidents be prioritized?
To ensure that incidents with the highest business impact are resolved first.
96. Identify the service management dimension focused on the communication systems and knowledge bases used by employees.
Information and technology.
97. Identify the service management dimension which is focused on an organization’s relationships with other organizations to deliver its services.
Partners and suppliers.
98. The IT department plans on installing a new application for all users over the weekend. What deployment approach is this called?
This is a Big Bang deployment.
99. What is the primary function of value chain activities?
Service value chain activities receive and provide triggers for further actions to be taken.
100. What does the ‘service request management’ practice depend on for maximum efficiency?
Processes and procedures.
101. Identify an item that refers to an outcome description.
Results for a stakeholder.
102. What practice ensures accurate and reliable information about configuration items and their relationships is available?
Service configuration management.
103. What usually requires a separate process?
Managing major incidents.
104. Service actions are performed by the service provider according to the…?
The agreement with the consumer.
105. What events allow actions to be taken before the business actually experiences any negative impact?
Warning events.
106. What is it called when components are integrated, tested, and deployed when needed, providing frequent opportunities for customer feedback loops?
Continuous delivery
107. What does the W stand for in a SWOT analysis?
Weakness.
108. What changes are low-risk, pre-authorized changes that are well understood and thoroughly documented and can be implemented without needing additional authorization?
Standard changes.
109. What is a list of minimum requirements that a service or service component must meet to be acceptable to key stakeholders?
Acceptance criteria.



